To increase access security, IHSE offers optional Two Factor Authentication (2FA) for switching via Draco tera KVM matrices. This allows a secure, user-specific login to the matrix.
Data security is one of the most important topics of recent times, especially in the field of critical infrastructures. As soon as workstations or consoles are equipped with access rights to various computers, there is a potential risk of unauthorized access, which in the worst case can lead to data theft or corruption.
In line with our strategy of maximum data security and by sharing with customers the need for maximum protection against unauthorized access and data leaks, we have integrated a two-factor login option for switching operations into our Draco tera KVM matrices.
Assigning access rights via the matrix
 In addition to completely open KVM networks, IHSE provides the possibility to assign access rights to certain consoles for certain CPUs; or to secure switching operations via the matrix with a username and password entry. Password authentication can be set for each switching operation or for each new logon to the matrix.
In addition to completely open KVM networks, IHSE provides the possibility to assign access rights to certain consoles for certain CPUs; or to secure switching operations via the matrix with a username and password entry. Password authentication can be set for each switching operation or for each new logon to the matrix.
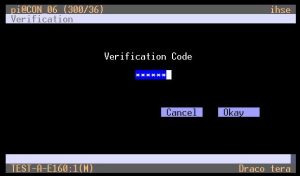 To ensure that only the authorized user enters his or her password, two factor authentication requires the entry of a 6-digit code after password entry. This code is generated via an authentication app on the smartphone and changes every 30 seconds. If the code matches against the matrix, the barrier opens: the user is logged in and can perform switching operations via the matrix.
To ensure that only the authorized user enters his or her password, two factor authentication requires the entry of a 6-digit code after password entry. This code is generated via an authentication app on the smartphone and changes every 30 seconds. If the code matches against the matrix, the barrier opens: the user is logged in and can perform switching operations via the matrix.
As flexible as possible and as secure as necessary
The different and simultaneous requirements for a high-end KVM system lead to a paradoxical situation: IHSE KVM systems have to be as easy and flexible to use as possible with fast, uncomplicated access. At the same time, however, they have to offer the highest security standards and provide maximum protection against unauthorized access. With the right features, these competing requirements can be met in a customer- and application-specific manner. We have also succeeded in this balancing act with 2FA, and we continue to work on increasing data security without sacrificing flexibility.
User-specific activation
The special feature of 2FA is its flexibility in use. Activation can be optionally set up for specific users, such as system administrators who potentially have access rights to all sources.
The authentication system works completely autonomously, requiring no Internet connection – just a cell phone with an authentication app.
In addition, no special IHSE tools are required. Common authentication apps (e.g. Google, Microsoft or LastPass Authenticator, Authy, etc.) make it easy to log in to the matrix.
