Mark Hempel
Head of Production Management
TRUE KVM: Making keyboard video mouse systems secure by design
The objective for the previous Part 1, Part 2 and Part 3 were to provide an introduction what we mean by relying on a Secure Core architecture for a TRUE KVM system by introducing 7 hypothesis for evaluating solutions.
These are
- Technically, KVM systems can be separated into two technical solutions which are very close to each other in terms of system performance.
- Commercially, open standard solutions typically offer lower cost of acquisition (larger markets provide better economies of scale).
a. Lower capex for IP based systems.
b. Difficult to assess, hidden operating cost during system lifetime.
c. Some customers don´t take this total cost of ownership (TCO) into account. - KVM systems support a wide variety of applications with varying needs of security.
a. Public safety and military applications.
b. This is now expanded to include what is coined critical infrastructures (public safety, military, power and water supply, core telecommunication infrastructures).
c. Mission critical commercial process control in nearly any industry vertical.
d. Non mission critical commercial and governmental applications (office infrastructures with limited real-time needs). - Increasing number of cyber-attacks within connected IP networks (aka the Internet), generally increase the risk of wide area and large-scale network outages.
- Most cyber-attacks exploit technical and human or process vulnerabilities and are, as such, difficult to defend against.
- Increasing number of intelligent devices with automatic machine communication (IoT, IIoT, M2M communication, autonomous driving, etc.) increases traffic volume and mixes physical and logical network infrastructure thus increasing the overall risk of being a victim of a successful attack.
- The discussion about technology selection is more driven by the needs of suppliers not the needs of users and customers.
In Parts 1 through 3, we addressed the first 5 and in this Part 4, we are going to continue to evaluate the next 2 hypothesis relevant for a secure operation of KVM systems.
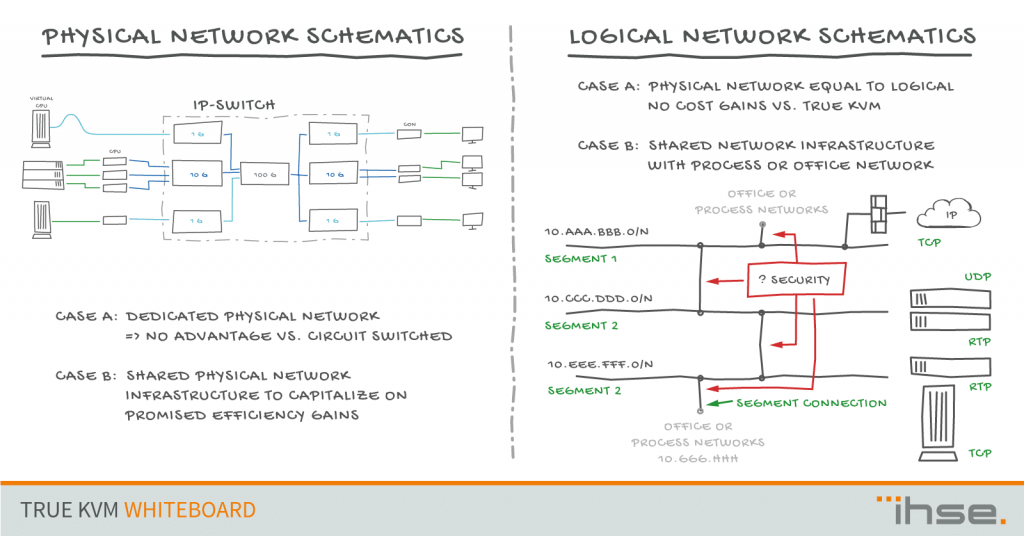
The main objective of this part is to raise awareness to the fact that, unlike Direct Connect KVM switching systems, IP based systems require two layers to describe the infrastructure. The first layer describes the physical wiring of the network determining which network elements are directly connected to each other. The second layer describes the logical network. Since one physical connection in an IP network can handle multiple logical connections separated by traffic protocol information. Though the analogy may not be perfectly accurate, but you should think of a network schematic connecting different applications. One application may be connected via various network switches using the same wiring and network elements as another application.
Addressing Hypothesis 6 and 7
A ubiquitous protocol like IP attracts a large user base and device population. Even in critical infrastructures like electrical power grids, metering devices and smartgrid controllers will rely on IP connections to perform their duties. Shielding the operations center from malicious upstream data traffic is key. In order to remain in operational control, the control room KVM system has to remain intact and operable at all times. The firewall/gateway between the KVM operated control system and the many devices and applications is of paramount importance. Something that is extremely hard to maintain in mixed usage scenarios when for example office and process network share the same infrastructure.
While dedicated systems have a clear relationship between physical cabling network and carried payload application data, IP systems require a physical connectivity and logical separation of networks. This requires a strictly IT based thinking. Additionally, it requires legacy knowledge of the application or production process and going forward an increased sensitivity for security measures and a relentless enforcement of them.
While dedicated systems have a clear relationship between physical cabling network and carried payload application data, IP systems require a physical connectivity and logical separation of networks. This requires a strictly IT based thinking. Additionally, it requires legacy knowledge of the application or production process and going forward an increased sensitivity for security measures and a relentless enforcement of them.
Using one infrastructure and an open standard IP network with off the shelve components offers significant savings. Connecting various network segments and mixing office and process or production network creates significant security exposure. With the increase of connected devices, guest networks and connected campus network islands, it becomes increasingly difficult to ensure a robust network security based on software protocols or ports as well as firewalls.
Operators of critical infrastructures have begun to strictly enforce a separation at least via firewalls. However, it is becoming more prominent to physically separate the networks. This however means co-locating switches for both networks, process and office, and requires separate cabling, which diminishes the advantage of a lower cabling cost.
When selecting a KVM system, always start with the application and the process in mind. The KVM solution should make the production easy, safe and cost effective over the entire life of the system. Connectivity into the IP world is a mandatory prerequisite. Gateways can handle this perfectly fine. Before deciding for an IP based system, assess risks and vulnerabilities, cost of ownership as a result of business needs. Not the other way around.
If you would like to discuss TRUE KVM with me in more detail, please leave a comment, send me a message or contact our technical support or sales teams at an IHSE office near you. We are here to help you get the most out of your KVM system.
Yours
Mark Hempel