Mark Hempel
Head of Production Management
TRUE KVM: Making keyboard video mouse systems secure by design
The objective for the previous Part 1 and Part 2 were to provide an introduction what we mean by relying on a Secure Core architecture for a TRUE KVM system by introducing 7 hypothesis for evaluating solutions.
These are
- Technically, KVM systems can be separated into two technical solutions which are very close to each other in terms of system performance.
- Commercially, open standard solutions typically offer lower cost of acquisition (larger markets provide better economies of scale).
a. Lower capex for IP based systems.
b. Difficult to assess, hidden operating cost during system lifetime.
c. Some customers don´t take this total cost of ownership (TCO) into account. - KVM systems support a wide variety of applications with varying needs of security.
a. Public safety and military applications.
b. This is now expanded to include what is coined critical infrastructures (public safety, military, power and water supply, core telecommunication infrastructures).
c. Mission critical commercial process control in nearly any industry vertical.
d. Non mission critical commercial and governmental applications (office infrastructures with limited real-time needs). - Increasing number of cyber-attacks within connected IP networks (aka the Internet), generally increase the risk of wide area and large-scale network outages.
- Most cyber-attacks exploit technical and human or process vulnerabilities and are, as such, difficult to defend against.
- Increasing number of intelligent devices with automatic machine communication (IoT, IIoT, M2M communication, autonomous driving, etc.) increases traffic volume and mixes physical and logical network infrastructure thus increasing the overall risk of being a victim of a successful attack.
- The discussion about technology selection is more driven by the needs of suppliers not the needs of users and customers.
In Part 1 and 2, we addressed the first 3 and in this Part 3, we are going to continue to evaluate the next 2 hypothesis relevant for a secure operation of KVM systems.
Addressing Hypothesis 4 and 5
Whether you are entrusted with the well-being of the population of your country or the seamless operation of the production plant, it is wise to carefully assess your needs in terms of network security and the operational implications. ISO27000 attempts to provide a step by step process to help IT teams managing the mission critical infrastructure of a company. It is also expected that ISO27000 will become for critical infrastructure what ISO9000 was for the commercial businesses.
“The world is being divided into those who know they are being hacked and those who don´t. However, everybody is subject to being hacked.” Once you acknowledge this inescapable truth I learnt during the presentation of a datacenter manager several years ago, you know you have to take the necessary precautions to shield your system against hacking exploiting unidentified operating system loopholes sold on the darknet.
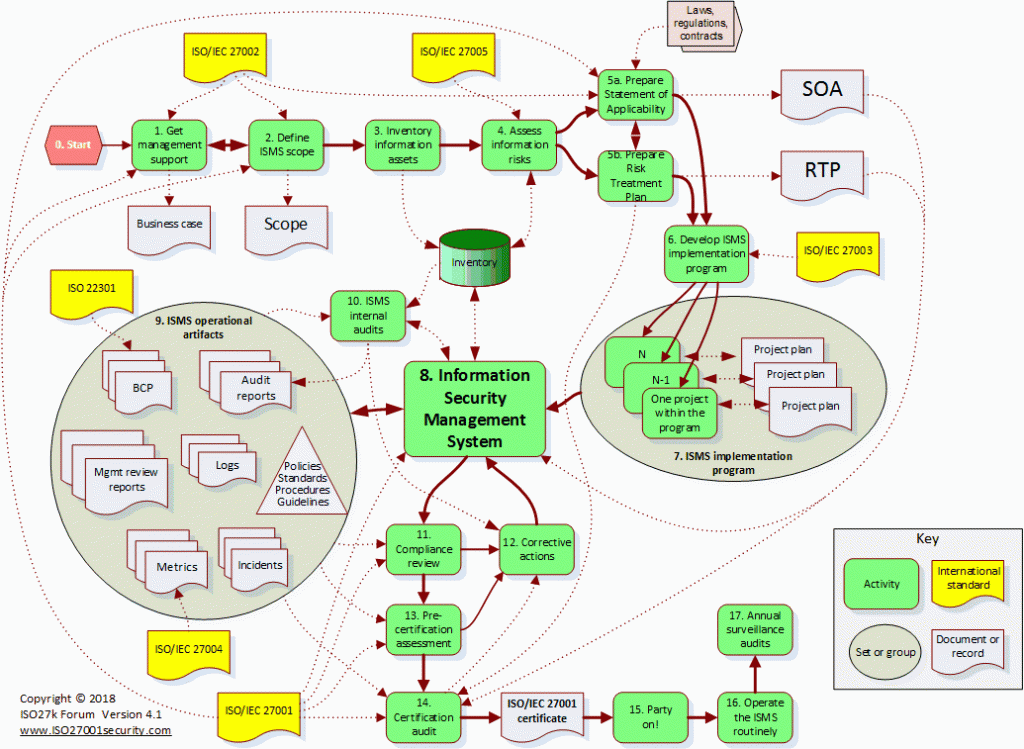
As mentioned above, take a step back and look at the security challenge holistically. Saving cost becomes irrelevant in the situation of a catastrophic failure. The guiding principle should be the definition of adequate protection first and then going into the details. Many penetrations occur based on human error and ill-guided attempts of users to take workflow shortcuts to save time. The following diagram is terribly complicated, I agree. But it offers a checklist and a framework to assess risks and implement measures to mitigate them. It is not only applicable to KVM infrastructure but serves as a blueprint for all operational networks connected to the internet. Many technical conclusions render separated cable networks and infrastructure components as the only viable solution to effectively protect assets and the integrity of the operation or mission.
Network protection is not only a technical effort. It involves regulation, procedures, training and an increased awareness of everyone in the company or operation for potential intrusion opportunities. It permeates all areas and levels and requires that everyone participates actively in the protection and enforcement of security.
If you would like to discuss TRUE KVM with me in more detail, please leave a comment, send me a message or contact our technical support or sales teams at an IHSE office near you. We are here to help you get the most out of your KVM system.
Yours
Mark Hempel